Scam artists will stop at nothing to make an extra buck, which means that people need to be vigilant about protecting their valuable information. While the phone is still a popular method of approach, the Internet has opened a new avenue for the scammer to attempt to steal your money.
Youth: the real tech-scam victims
The truth about Unified Communications
Many business owners wonder whether Unified Communications (UC) would ultimately benefit their business. If you are one of those business owners, get to know some of the facts about UC before you make your ultimate decision. Read on for information on the pros and cons of UC and contact us as soon as you are ready to make your choice.
Small business & the laptop vs desktop debate
With the advent of e-commerce and online storefronts, global commerce has opened a whole new world for the small business owner. It has never been easier to find customers for your product or service. Of course, you still need to have to right tools.
Untapped social media options
Facebook, Twitter, and Instagram have changed the way we interpret the word social. Whereas it used to mean just catching up with a friend over tea, being social online now has blurred the lines between friends and customers. But far beyond the “big three” lies dozens of untapped social networks.
Enjoy Opera 41’s browsing features
In a world full of fresh options, there is no reason for you to be bogged down by outdated methods. It helps to have the latest web browser tools to improve your online experience. Exploring other options always brings out revelations about how you can improve your business.
Why BI Software is a wise pick for your company
With Business Intelligence software, companies have the ability to pull data from various sources throughout the company, from human resources to accounting and marketing reports. By combining information from across departments, owners have all the data they need to make the best decisions for their company.
Download iOS 10.1 right now and here’s why
If you want to make sure that your iPhone reliably works the way it should and that all the information in it is secure, you should always pay special attention to updates as soon as they become available. Although you may be hesitant to immediately download the latest iOS 10.1 update, you should get to know more about why you should download this update right away.
How Outlook’s update Improves User Experience
When it comes to the communications tools you use in your business, there may be many opportunities to improve the process that you have not yet explored. Microsoft Outlook has made improving your use of communications technology even easier with its latest changes and updates.
Malware hits more than 3,000 Android apps
There is a new threat to Android users that has many customers racing to their closest IT security firm. The malware, from the DressCode family, makes a subtle entrance through Android apps and then branches off to attack your most sensitive files. Here is more information on the vicious DressCode malware and how you can safeguard your computer from infiltration.
500 Million Yahoo Users Affected by Data Breach – Password Change Recommended
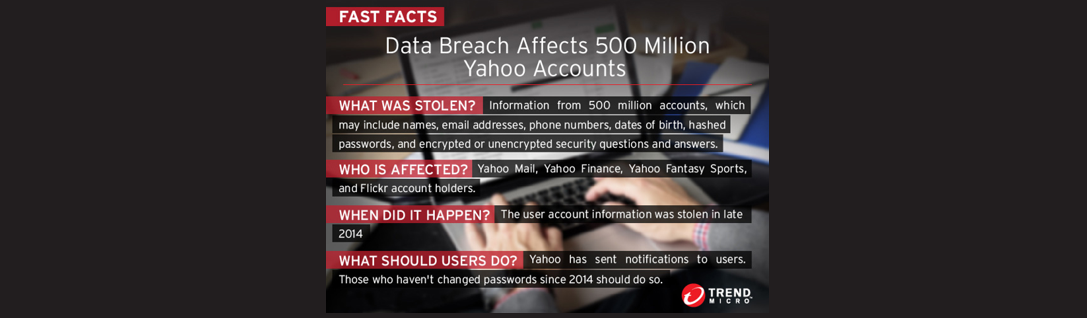
Source: Trend Micro
Yahoo has confirmed a massive breach that compromised the personal information of 500 million of its users, affecting account holders of Yahoo Mail, Yahoo Finance, Yahoo Fantasy Sports, and Flickr. The tech giant was quick to issue a plan of action, with Yahoo chief information security officer Bob Lord posting an announcement on Tumblr on September 22. The post outlines the investigation, a protection plan, and security recommendations.